Huawei Hacked My Laptop? |
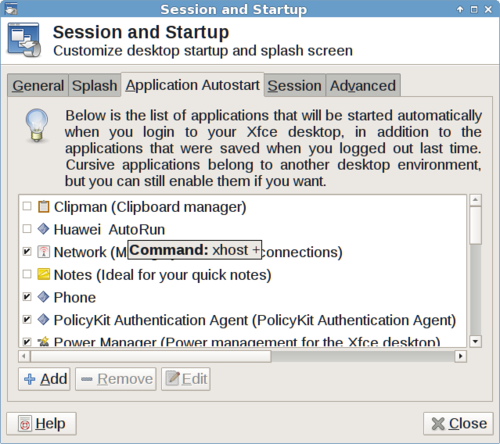
The screenshot above shows a script called "Huawei Autorun" which executes the command "xhost +" when you login. This command makes your Linux desktop remotely accessible to anyone on the network. The "Huawei Autorun" script appeared on my laptop after installing a Huawei E353 HSPA+ 3G USB stick (with serial number CE0682 on the back).
It seems like I dodged a bullet as I don't use the standard Linux GNOME desktop, so the script was not enabled, but the fact remains that Huawei installed malware on my Linux laptop. If they managed to get into my laptop, imagine what is happening inside your phone.
State-sponsored hacking is real.
----UPDATE----
For those people who requested more information. The OS is Debian 8.1 LTS. The script is basically a one-liner embedded in an autostart launcher (see below). It was installed as root, so I must have screwed up big time there. Obviously, I'll have to reinstall my OS. Debian 8 is at end of life now anyway.
$ cat /etc/xdg/autostart/HuaweiAutoStart.desktop [Desktop Entry] Version=1.0 Encoding=UTF-8 Name=Huawei AutoRun Name[en_US]=Huawei AutoRun Exec=xhost + SwallowExec= SwallowTitle= Terminal=false TerminalOptions= Type=Application URL= X-KDE-SubstituteUID=false X-GNOME-Autostart-enabled=true GenericName[en_US]=
----UPDATE 2----
Okay, I decided to check out this modem. It does include Linux drivers which require root for installation. I reran the installation script as root and sure enough the same autostart script was reinstalled.
$ ls /etc/xdg/autostart/ -l
total 116
-rw-r--r-- 1 root root 305 Oct 10 2014 at-spi-dbus-bus.desktop
-rw-r--r-- 1 root root 6351 Oct 21 2014 gnome-keyring-gpg.desktop
-rw-r--r-- 1 root root 7777 Oct 21 2014 gnome-keyring-pkcs11.desktop
-rw-r--r-- 1 root root 7339 Oct 21 2014 gnome-keyring-secrets.desktop
-rw-r--r-- 1 root root 5996 Oct 21 2014 gnome-keyring-ssh.desktop
-rw-r--r-- 1 root root 7741 Aug 27 2014 gsettings-data-convert.desktop
-rwxr-xr-x 1 root root 262 Jul 25 23:59 HuaweiAutoStart.desktop
....
This script is also installed to $HOME/.config/autostart/HuaweiAutoStart.desktop. Another script called ReadDisplay is installed in /usr/local/modem which passes the $DISPLAY environment variable to a binary called MobilePartner. The drivers do include a GUI, but if the sole purpose of all this is to fire up a GUI then it is not only exceptionally sloppy code, but also a security risk that needs explaining.
Below is a tarball image of the huawei e353 drivers so you can audit them for yourself. I've included the Windows drivers so you get an image of the disk just as I have it. Heck you could even try it for yourself. The drivers didn't compile the second time I did this, but the autostart script was still installed.
Download huawei e353 drivers (warning, possible malware!)
----UPDATE 3----
I'm giving Huawei the benefit of doubt on this one. As a commenter suggested, it is probably a hack to run the GUI as root. Either way, it is still a nasty vulnerability, even if your X server is configured to use local sockets by default. I guess this shows the folly of blindly trusting hardware manufactures. I'll be sticking to open source code from official repositories in the future.
Live and learn, I suppose.
Huawei Hacked My Laptop?About Sunburnt Technology
Sunburnt Technology has been helping businesses reach customers around the world since 2003. Our integrated Internet Business Platform includes SEO Tools, Web Analytics, Content Management, Website Designer, Email Marketing, Online Store, Domain Name Management and more. |
| Back to Blog | The Game Of Your Life » |
